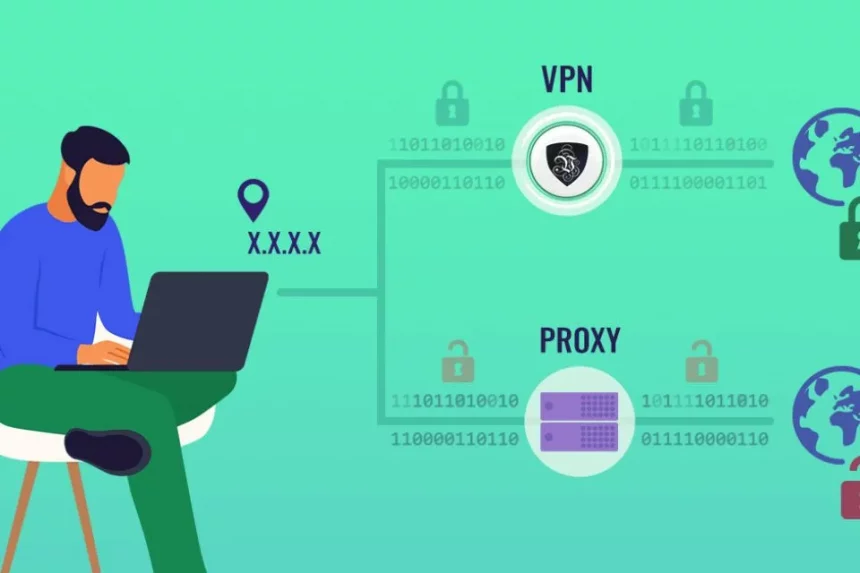
In today’s digital world, data security is of utmost importance. An important element of data security is the use of a proxy server. A proxy server acts as an intermediary between a client computer and the internet, allowing the client computer to communicate with the internet while keeping its identity and IP address hidden. It also provides an added layer of security by filtering data requests and preventing malicious attacks. Without a proxy server, your network is vulnerable to a variety of threats, including data theft, disruption of services, and malicious attacks, making it critical to incorporate a proxy server into your security strategy. In this article, we’ll explore the importance of having a secure proxy server, how it works, and the benefits it can provide for your organization.
In today’s digital world, data security is of utmost importance. An important element of data security is the use of a proxy server. A proxy server acts as an intermediary between a client computer and the internet, allowing the client computer to communicate with the internet while keeping its identity and IP address hidden. It also provides an added layer of security by filtering data requests and preventing malicious attacks. Without a proxy server, your network is vulnerable to a variety of threats, including data theft, disruption of services, and malicious attacks, making it critical to incorporate a proxy server into your security strategy. In this article, we’ll explore the importance of having a secure proxy server, how it works, and the benefits it can provide for your organization.
What is a Proxy Server and How Does It Work?
A proxy server is a computer or network service that acts as an intermediary between a client computer and the internet. It allows the client computer to communicate with the internet while keeping its identity and IP address hidden. It also provides an added layer of security by filtering data requests and preventing malicious attacks.
The proxy server acts as a middleman between the client computer and the internet. It receives requests from the client computer for data, websites, and other resources, then forwards those requests to the internet. The proxy server then sends the requested data back to the client computer.
- Advertisement -
The proxy server also provides an additional layer of security by filtering data requests and blocking malicious attacks. It can also be used to bypass certain restrictions and censorship, and to access websites and services that are blocked in certain countries.
Benefits of Using a Proxy Server
Using a proxy server can provide many benefits for your organization. It can provide an added layer of security by blocking malicious attacks, preventing data theft, and protecting your network from disruption of services.
It can also improve your network performance by caching frequently requested data and websites, allowing them to be accessed faster. This can also reduce the strain on your network resources, allowing you to devote more resources to other tasks.
Using a proxy server can also help you bypass certain restrictions or censorship. This can be especially useful if your organization is located in a country with strict internet regulation.
Finally, using a proxy server can help you access websites and services that are blocked in certain countries. This can be especially helpful if you need to access certain resources from outside sources.
Different Types of Proxy Servers
There are several different types of proxy servers, each with its own set of features and benefits. The most common types of proxy servers are:
- Shared Proxy Server: A shared proxy server is a server that is shared by multiple users. It is generally used for web browsing and can be used to bypass certain restrictions and access websites and services that are blocked in certain countries.
- Dedicated Proxy Server: A dedicated proxy server is a server that is dedicated to a single user or organization. It is more secure than a shared server and is usually used for more sensitive data.
- Virtual Private Network (VPN): A VPN is a secure, encrypted connection between two computers over the internet. It is used to access resources securely, bypass restrictions and censorship, and access websites and services that are blocked in certain countries.
How to Choose the Right Proxy Server for Your Organization
Choosing the right proxy server for your organization can be a daunting task. There are several factors to consider, including security, performance, cost, and availability.
The first step is to determine your organization’s needs. Are you looking for a shared proxy server for web browsing, a dedicated server for more secure data, or a VPN for secure connections? Once you’ve determined your organization’s needs, you can narrow down your options.
The next step is to consider the security of the proxy server. Make sure the server you choose is secure and meets your organization’s security requirements. You should also consider the performance of the server. Make sure the server is able to handle the amount of traffic your organization requires.
Finally, consider the cost and availability of the server. Make sure the server is affordable and available when you need it.
Security Risks of Not Using a Proxy Server
Not using a proxy server can leave your organization vulnerable to a variety of security threats. Without a proxy server, your network is exposed to data theft, disruption of services, and malicious attacks.
Data theft is a serious threat to any organization. Without a proxy server, malicious attackers can easily steal sensitive data such as passwords and credit card numbers.
Another threat is disruption of services. Without a proxy server, malicious attackers can disrupt services such as email and web hosting. This can have a significant impact on your organization’s operations.
Finally, without a proxy server, your organization is vulnerable to malicious attacks such as viruses and malware. These attacks can cause significant damage to your network and data.
Best Practices for Using a Proxy Server
Using a proxy server can provide many benefits for your organization, but there are also risks associated with using a proxy server. To ensure the security of your network, it’s important to follow best practices when using a proxy server.
The first step is to make sure you choose the right proxy server for your organization. Make sure the server is secure and meets your organization’s security requirements.
The next step is to make sure the proxy server is properly configured. Make sure the server is configured correctly and that all security settings are enabled.
Finally, make sure you keep the proxy server up to date. Make sure the software and firmware are up to date and that any security patches are applied.
Common Threats a Proxy Server Can Protect Against
A proxy server can provide an additional layer of security for your organization. It can protect your network from a variety of threats, including data theft, disruption of services, and malicious attacks.
Data theft is a serious threat to any organization. A proxy server can help protect your network from data theft by blocking malicious requests and filtering data requests.
Another common threat is disruption of services. A proxy server can help prevent disruption of services by blocking malicious requests and filtering data requests.
Finally, a proxy server can help protect your network from malicious attacks such as viruses and malware. It can filter out malicious requests and block malicious traffic, helping to protect your network from these threats.
Strategies for Implementing a Secure Proxy Server
Implementing a secure proxy server can be a daunting task. To ensure the security of your network, it’s important to develop a strategy for implementing a secure proxy server.
The first step is to determine your organization’s needs. Are you looking for a shared proxy server for web browsing, a dedicated server for more secure data, or a VPN for secure connections?
The next step is to choose the right proxy server for your organization. Make sure the server is secure and meets your organization’s security requirements.
The next step is to configure the proxy server. Make sure the server is properly configured and that all security settings are enabled.
Finally, make sure you keep the proxy server up to date. Make sure the software and firmware are up to date and that any security patches are applied.
Conclusion
Using a proxy server can provide many benefits for your organization, including an added layer of security, improved network performance, and the ability to bypass certain restrictions and censorship. It is critical to incorporate a proxy server into your security strategy to protect your network from data theft, disruption of services, and malicious attacks.
When choosing a proxy server, it’s important to consider your organization’s needs, the security of the server, its performance, cost, and availability. It’s also important to follow best practices for using a proxy server and to keep the server up to date.
By following these strategies, you can ensure the security of your network and protect your organization from a variety of threats.